38 aws security best practices
Best practices for securing sensitive data in AWS data stores Read more about security zone modeling in the "Using Security Zoning and Network Segmentation" section of the AWS Security Best Practices whitepaper. By setting up security groups for each of your applications, you can model network security for your database by configuring the security groups to allow ingress traffic only from selected ... Learn best practices for securing your AWS account and resources Here are some best practices to consider when securing your account and its resources: Safeguard your passwords and access keys Activate multi-factor authentication (MFA) on the AWS account root user and any users with interactive access to AWS Identity and Access Management (IAM) Limit AWS account root user access to your resources
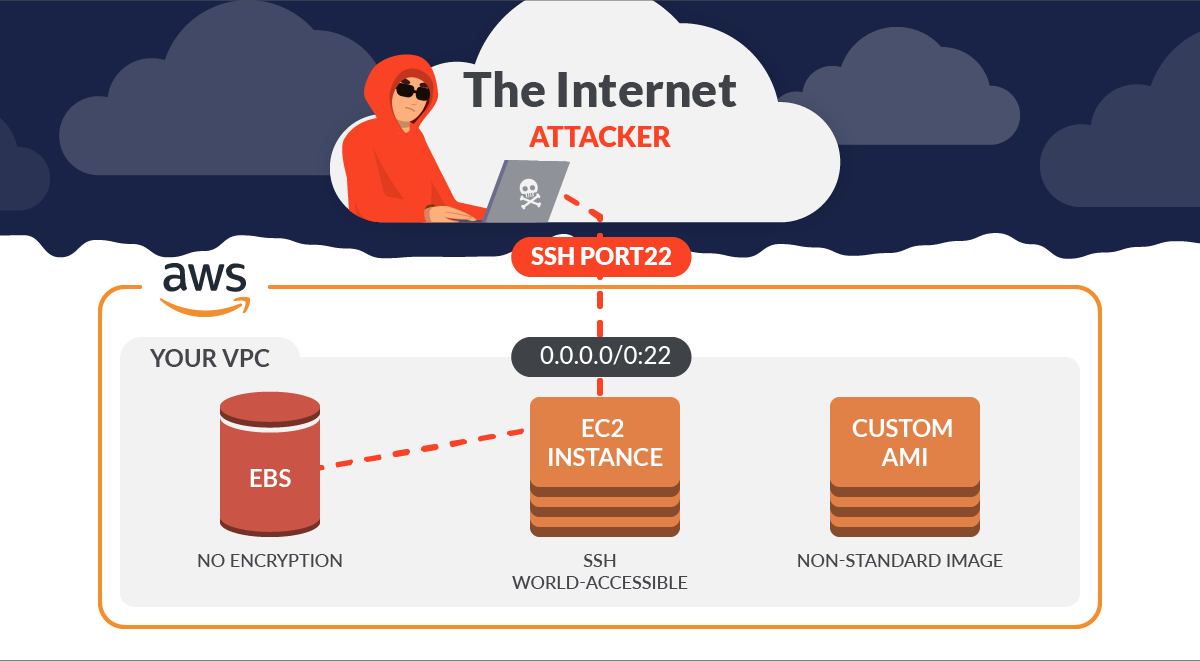
AWS S3 - Security Best Practices - Rently Engineering Blog So we need to follow the security best practices as discussed below. 1. Check for S3 bucket policies and block the public access. Assign S3 bucket policies and Access Control Lists (ACLs) for authenticated IAM users. S3 Bucket Policy. Block public access for S3 bucket. Block public access.
Aws security best practices
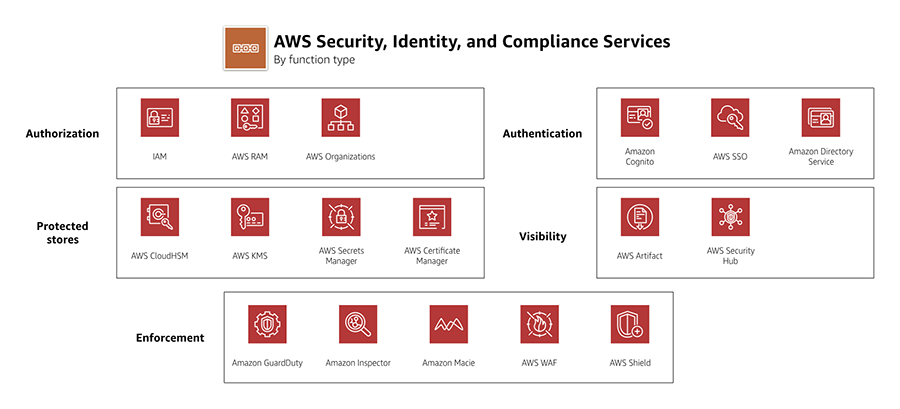
Security, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework. Best Practices for Manufacturing OT Security | AWS for Industries The AWS OT Security white paper covers the best practices for OT security. In this blog post, we touch on these best practices under the following broad topics: Secure all layers Secure network connections to the cloud Secure operational data Enhance traceability and observability Manage devices and gateways to shrink attack surface Security best practices for Amazon EKS - Amazon EKS Security groups for pods. Multiple network interfaces for pods. Metrics helper. Alternate compatible CNI plugins. Installing the AWS Load Balancer Controller add-on. Managing the CoreDNS add-on. Managing the kube-proxy add-on. Installing the Calico add-on.
Aws security best practices. AWS Security Best Practices Checklist - DZone Security AWS Cloud Security Best Practices. Tuning Redshift. The Top Ten Cloud Tools From AWS. AWS security Database Redshift (theory) cluster AI Data (computing) Virtual private cloud application ... AWS Cloud Security Best Practices: Securing AWS Environments - Rapid7 Having said that, if you understand the unique aspects of cloud security and apply best practices, AWS can be as secure as (or even more secure than) an on-premises network. The importance of strong AWS cloud security. Strong AWS security is important for the same reasons why cybersecurity in general is important. AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ... Top 10 AWS Security Best Practices - easydeploy.io 1.1 Top 10 AWS Security Best Practices 1.1.1 1. Know the Shared Responsibility Model for Security 1.1.2 2. Multi-factor Authentication 1.1.3 3. Identity and Access Management 1.1.4 4. Securing Database and Data Storage Services 1.1.5 5. File Integrity Monitoring 1.1.6 6. Improve CloudTrail Functionalities 1.1.7 7. SSL Certificates 1.1.8 8.
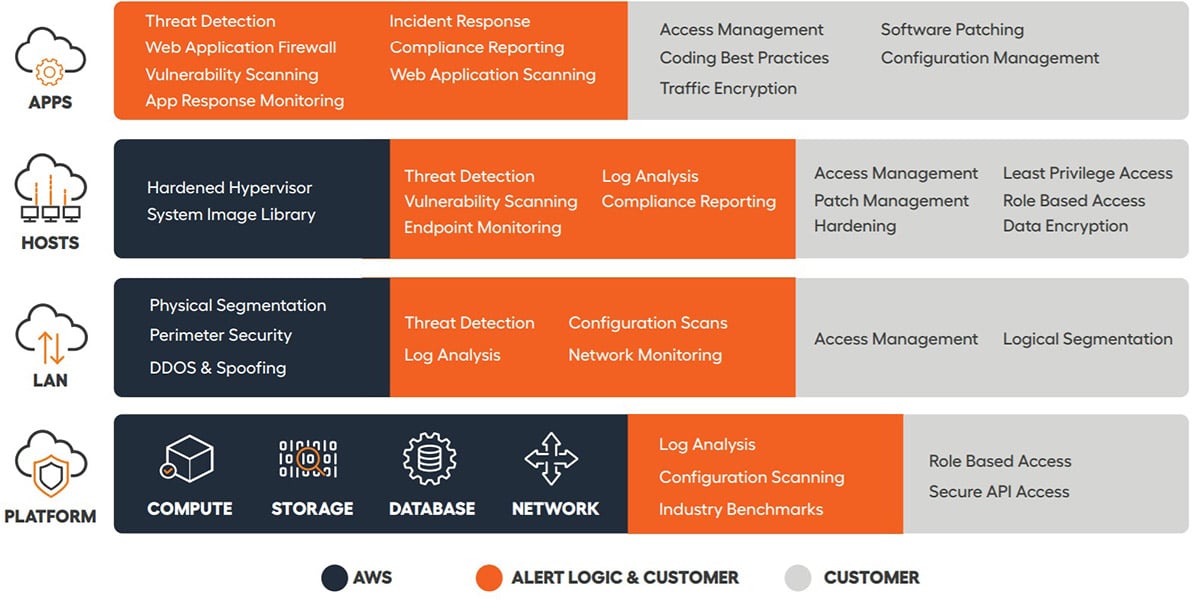
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist. 9 AWS Security Best Practices - Alert Logic [ Data Security Best Practices] 6. Backup Your Data You never know if you're going to need to restore data after a breach, so back up your data regularly. You can do this by using AWS Backup. This app makes it easy to automate backups across your AWS environment, so you never have to worry about losing important information. 9 AWS Security Best Practices: Securing Your AWS Cloud First of all, AWS security best practices are based on the above-mentioned shared responsibility model, which allows the vendor to direct additional resources to enhance their share of the security... AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
AWS Security Best Practices Checklist | CDWG Some practices may be as easy as performing regular data backups or creating appropriate password policies but can go a long way in increasing overall security. By following this checklist, you can help ensure that your cloud-based and in-house services are as secure as possible: 1. Create Strong Password Policies AWS Security Best Practices | Classroom Training | AWS Students should have familiarity with AWS services and a strong background in information security concepts, techniques, and paradigms in the areas of networking, operating systems, data encryption, and operational controls. We recommend that attendees of this course have completed: AWS Security Fundamentals AWS Security Essentials Find a class 8 of the Most Common AWS Security Mistakes to Avoid Making Eight common AWS security pitfalls. Misconfigured S3 buckets. Lack of horizontal access control on S3 objects. Dangling S3 subdomain takeover. Lack of logging. No custom IAM users and roles for specific actions with minimal privileges. No custom security groups for resources that need to communicate with each other. Top 8 AWS Security Best Practices for 2022 - snyk.io While this list is certainly not comprehensive, the following eight AWS best practices are the ones we have found to be most valuable to companies operating in the cloud. Cloud security controls Incident response planning Monitoring & alerting Encryption Data backups Up to date AWS Compliance planning Scaling security in workflows 1.
10 AWS Security Best Practices For Developers | YourTechDiet Here are the 10 AWS Security Best Practices for Developers. Enable AWS CloudTrail; AWS CloudTrail is a tool that allows you to record API logs for security analysis, compliance auditing, and change tracking. With it, one can create trails of breadcrumbs which lead back to the source of any changes made to your AWS environment.
What is AWS Security? Risks, Best Practices, and More - Digital Guardian Here are some best practices to help you choose the right solution: Easy integration. Choose a security solution that integrates with AWS to make the process painless. Maintain visibility and control. To be able to effectively audit and control compliance, choose a solution that allows total visibility and control.
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion.
21 AWS Security Groups Best Practices | McAfee Blog Definitive Guide to Securing Workloads on AWS Download to learn about the AWS adoption trends, security challenges and best practices around AWS and applications deployed in AWS. Download Now 6) Outbound access: Restrict outbound access from ports to required entities only, such as specific ports or specific destinations.
51 AWS Security Best Practices | McAfee Blog AWS infrastructure security best practices. 1) Familiarize yourself with AWS's shared responsibility model for security. Like most cloud providers, Amazon operates under a shared responsibility model. Amazon takes responsibility for the security of its infrastructure, and has made platform security a priority in order to protect customers ...
26 AWS Security Best Practices to Adopt in Production AWS Cloud security best practices checklist. In this section we will walk through the most common AWS services and provide 26 security best practices to adopt. AWS Security with open source - Cloud Custodian is a Cloud Security Posture Management (CSPM) tool. CSPM tools evaluate your cloud configuration and identify common configuration mistakes.
AWS Security Group: Best Practices & Instructions - CoreStack Best Practice. Using the AWS default security group for active resources. New instances can adopt the group by default - potential unintentional security compromise. Create new security groups and restrict traffic appropriately. Allow all inbound access (using 0.0.0.0/0) to some or all ports.
AWS Cloud Security Best Practices - Sysdig AWS Container Security Best Practices. Like other major public clouds, AWS offers several ways to run containerized applications. The primary AWS container services include: Elastic Container Service (ECS), a managed container service that is based on an orchestrator that Amazon developed itself. Elastic Kubernetes Service (EKS), a managed ...
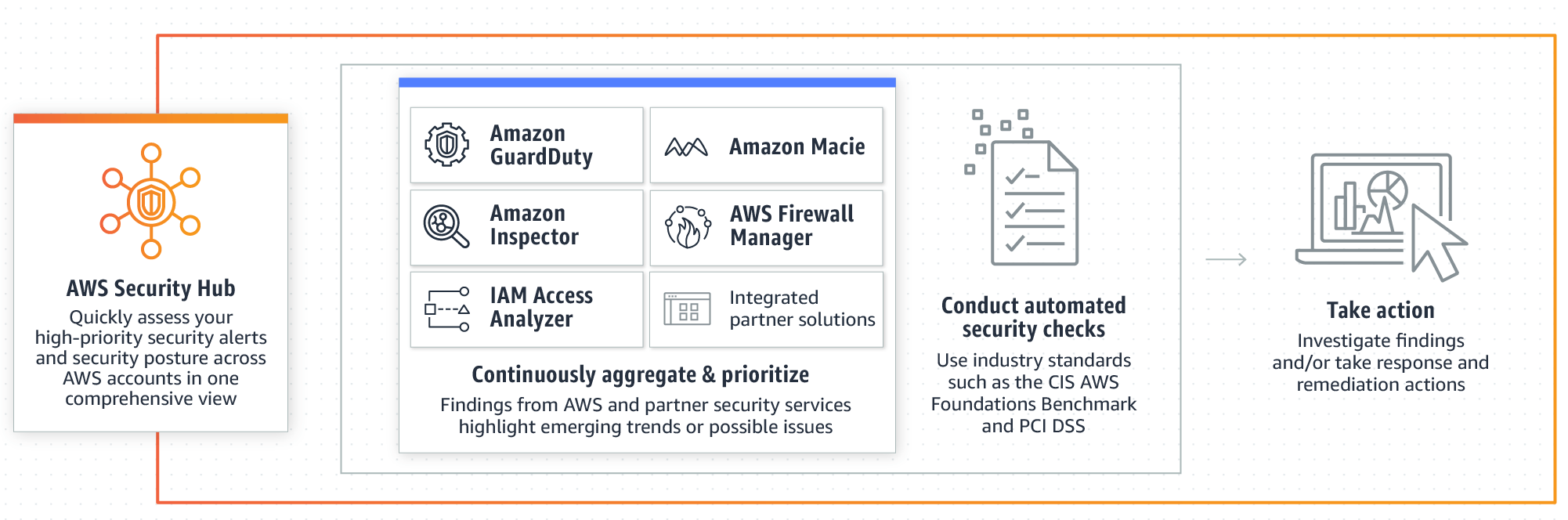
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices.
Security Best Practices for AWS Config - AWS Config Leverage tagging for AWS Config, which makes is easier to manage, search for, and filter resources. Confirm your delivery channels have been properly set, and once confirmed, verify that AWS Config is recording properly. For more information, see AWS Config best practices blog. Did this page help you? Provide feedback Edit this page on GitHub
Security best practices for Amazon EKS - Amazon EKS Security groups for pods. Multiple network interfaces for pods. Metrics helper. Alternate compatible CNI plugins. Installing the AWS Load Balancer Controller add-on. Managing the CoreDNS add-on. Managing the kube-proxy add-on. Installing the Calico add-on.
Best Practices for Manufacturing OT Security | AWS for Industries The AWS OT Security white paper covers the best practices for OT security. In this blog post, we touch on these best practices under the following broad topics: Secure all layers Secure network connections to the cloud Secure operational data Enhance traceability and observability Manage devices and gateways to shrink attack surface
Security, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework.









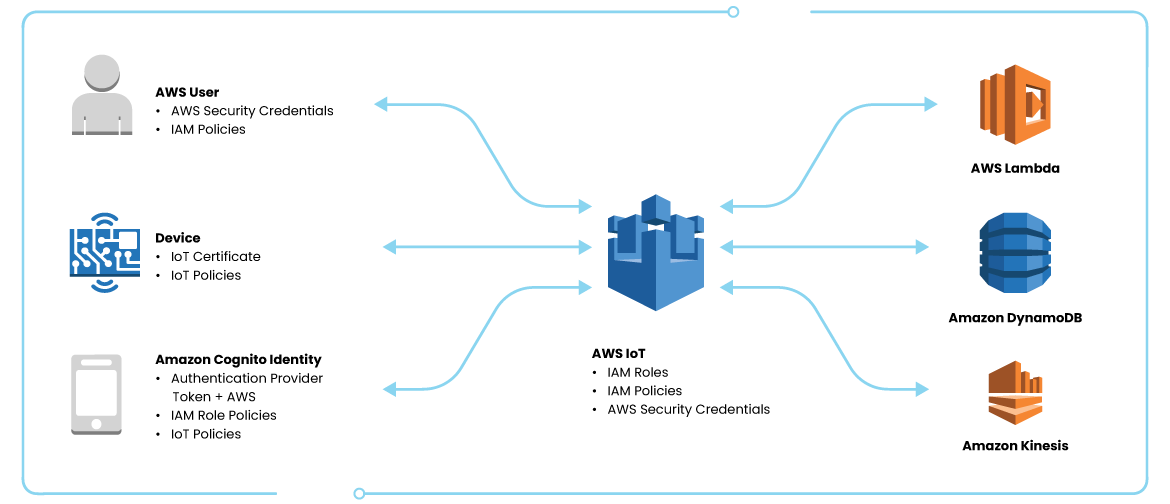

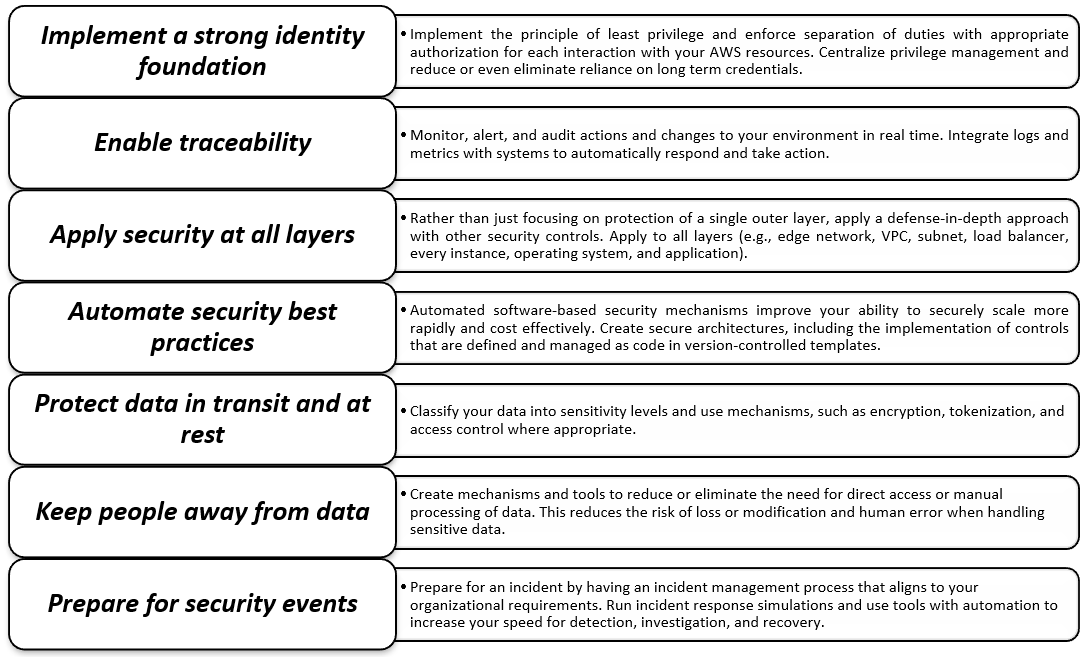


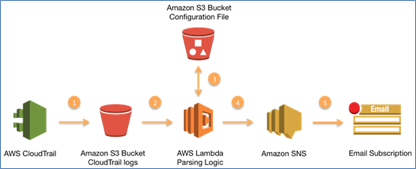

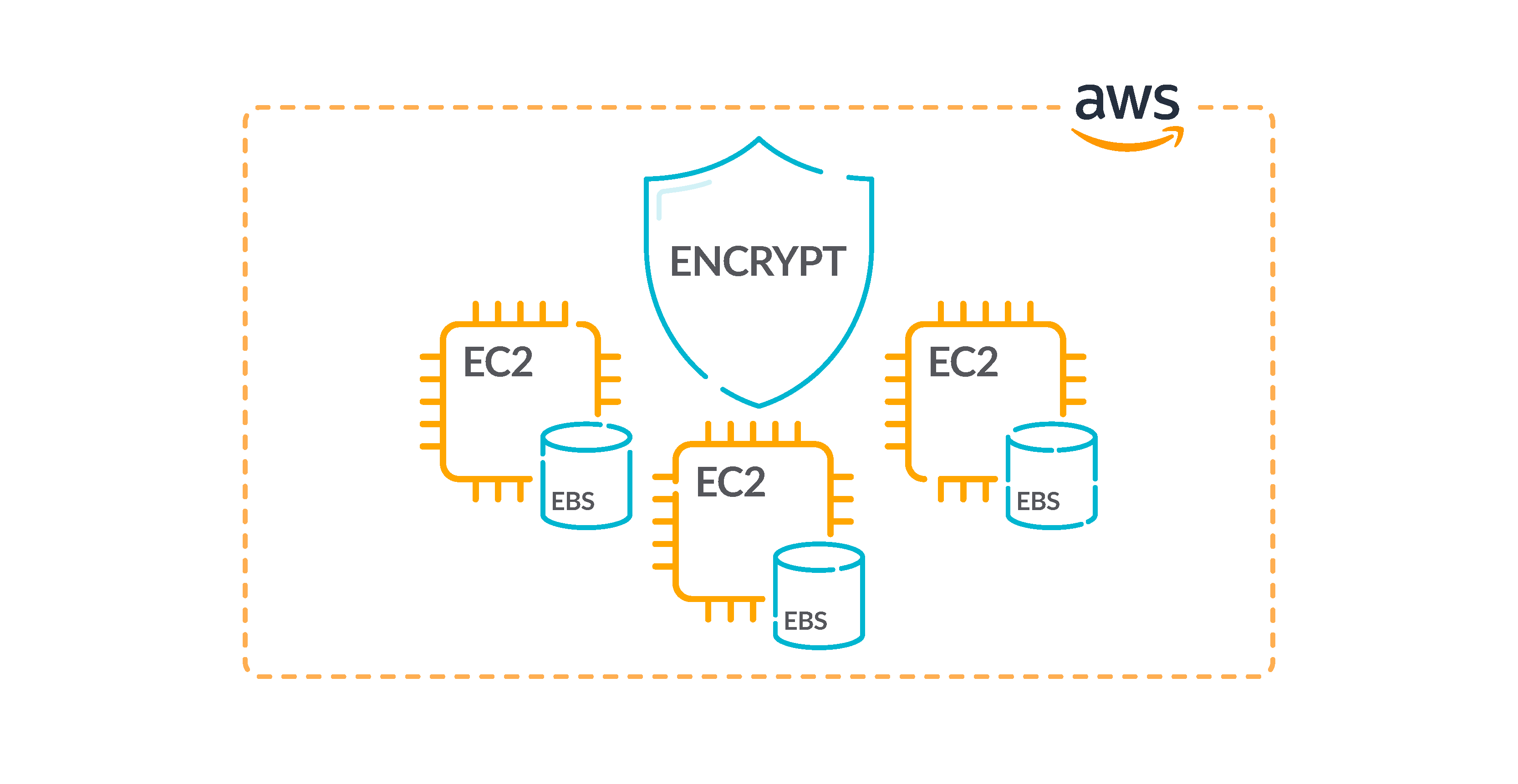










.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)
0 Response to "38 aws security best practices"
Post a Comment